Deploying a Tor Hidden Service with DigitalOcean
A quick primer on Tor hidden services
The Tor protocol picks 3 onion routers at random, builds circuits to them, treating them as introduction (or contact) points; since this is a circuit, there is no direct connection, so no IP addresses are shared, just public keys. These public keys work toward “shaking hands” at a rendezvous point. If the handshake happens, the rendezvous point connects Alice’s and Bob’s circuits, and then they can communicate anonymously. While the protocol isn’t without flaw, it is still powerful, especially when used in conjunction with other practices and tools. If you have sensitive information, it is your responsibility to ensure that your system is protected, and that your visitors are protected. Deploying a hidden service is a good step toward offering that protection.
Deploy the VPS with Digital Ocean
We are going to create a Debian Droplet on DigitalOcean. After creating my account, I fork up the $5 to create my Droplet—it would be cool if DigitalOcean gave a student discount for students to practice, but I digress.
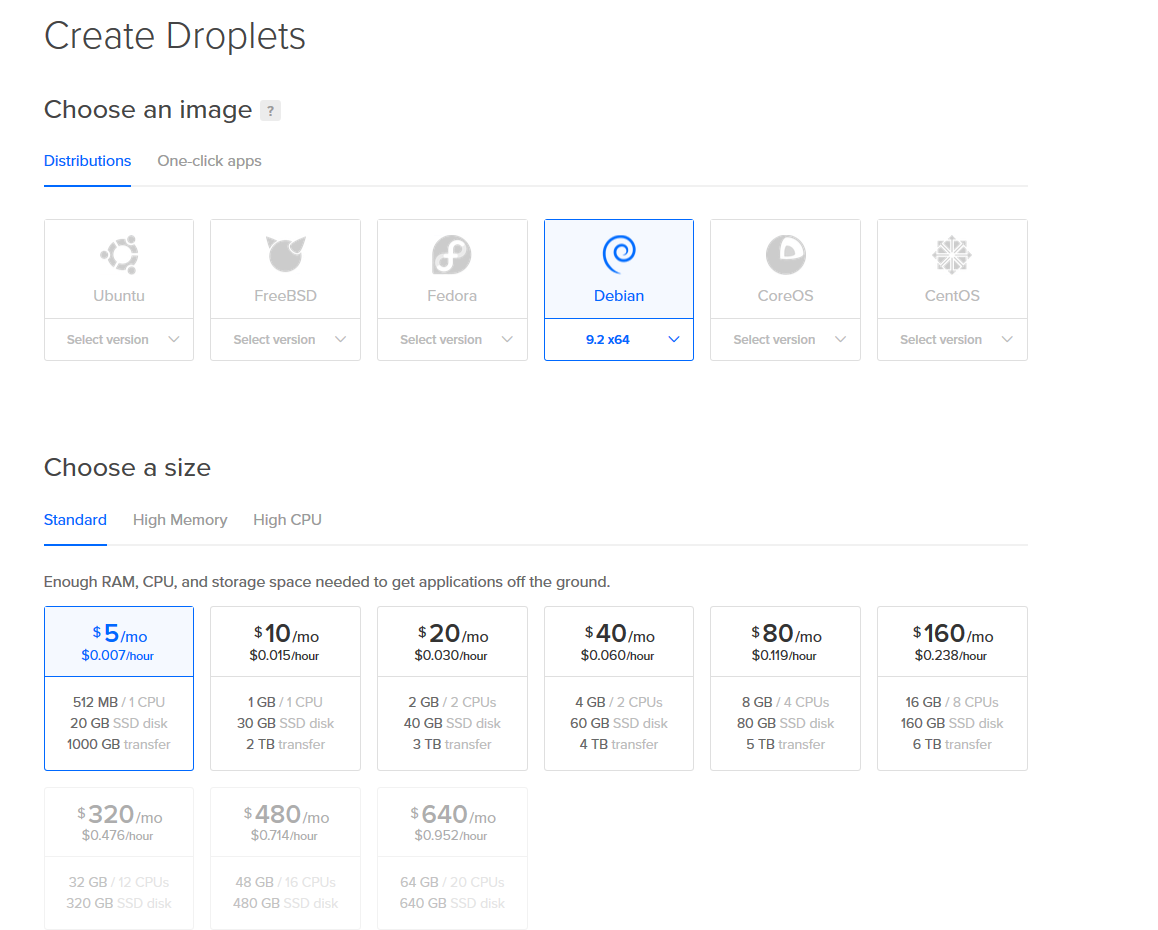
I chose not to add an SSH key, and I left the hostname at its default. If you are comfortable with SSH, feel free to add yours, but this tutorial assumes a lack of familiarity. Click that giant green Create button and the droplet should be created within the minute.
Set Up SSH for Securely Logging In
DigitalOcean has a solid tutorial on first steps for setting up SSH.
I generate a key and since I already have a (useless) key named id_rsa, I choose to overwrite it. I hit enter twice to get through the passphrase prompts. The key is generated (and some parts blanked out by me)—this generated randomart is supposed to make it easier for the user to verify that the key hasn’t been tampered with, otherwise they would have to compare long strings of text.
Because we created the droplet without an SSH key, DigitalOcean sent us an email with our username (likely root), droplet IP, and temporary password. I personally logged into the console through the DigitalOcean web-portal and changed my password to something else, but that isn’t necessary.
To copy your public key to your server Use ssh-copy-id username@ip. Note, your username will be root by default, counterintuitively. Use either the temporary password that was emailed to you, or your updated password if you went that route. Now you should be able to SSH into your server with ssh username@ip.
After successfully SSHing into your server, consider disabling password authentication on your server to prevent brute-force attacks. In the linked tutorial, at the bottom, under Disabling Password Authentication on your Server:
sudo nano /etc/ssh/sshd_config- Change from
PasswordAuthentication yestoPasswordAuthentication no sudo service ssh restart
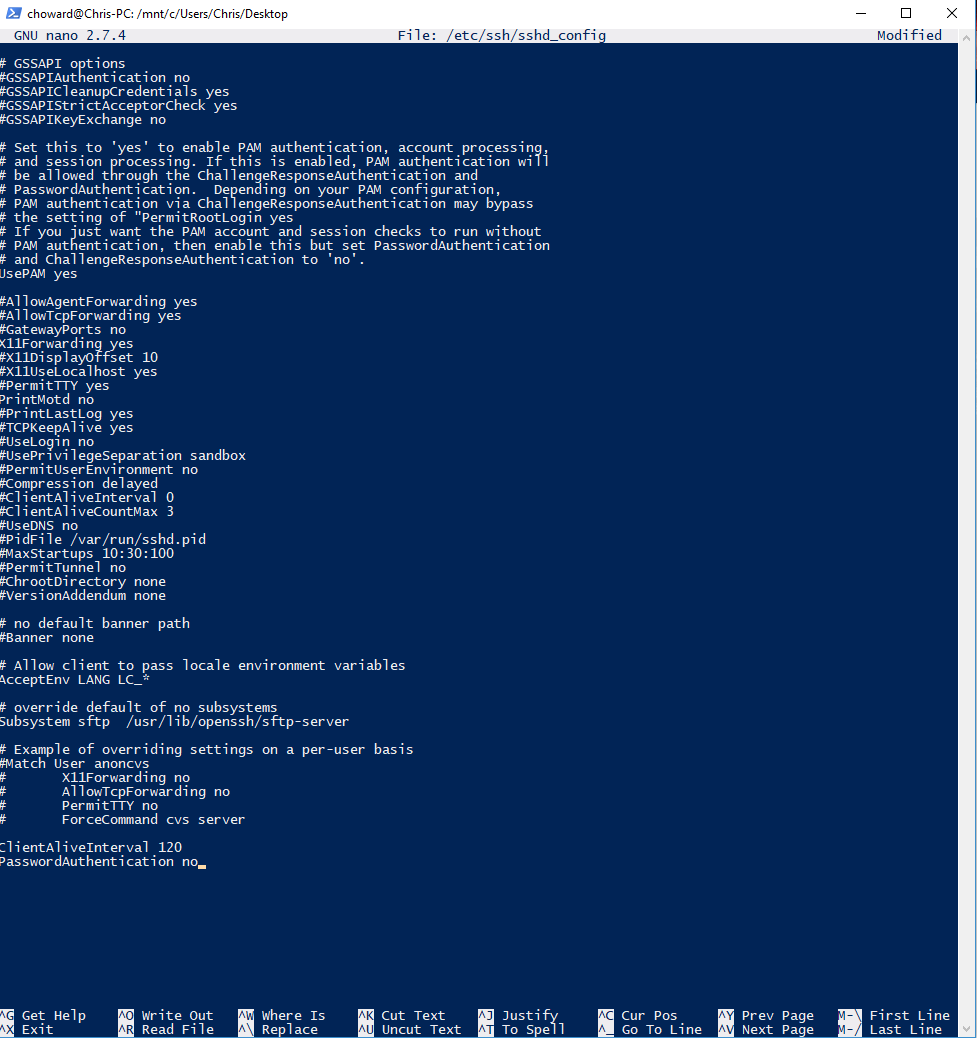
Now the only way to get into your server is SSH.
Install the Uncomplicated Firewall
ufw is a frontend for iptables, which is a firewall system for Linux, but simpler. ufw will be installed to at least reduce the number of attacks your server might get, as we are going to block most traffic. Chances of attack are pretty high, you can install Fail2Ban to scan and ban IP addresses associated with malicious activity (most of which will probably be Chinese). It’s better to get security stuff right early on. Also be mindful that Tor relays and exit nodes are also frequently attacked.
Run the following commands in your command line, while logged into your server:
sudo apt-get update
sudo apt-get upgrade -y
sudo apt-get dist-upgrade -y
sudo apt-get install ufwUpdating first will help you prevent running into this error:
Package ufw is not available, but is referred to by another package. This may mean that the package is missing, has been obsoleted, or is only available from another source
E: Package ‘ufw’ has no installation candidate
and you should be good to go. The firewall is installed. Now enable the firewall:
sudo ufw enable -y
sudo ufw statusStatus should output Status: active.
Create a New User Account
To be careful not to do something disastrous in the server, it is good practice to create a new, non-root user account, and to limit its privileges so that we reduce the likelihood of breaking something important. Additionally, using an alternative account and getting rid of the root account can also work toward preventing being brute-forced. Again, DigitalOcean has a nice tutorial on creating a new user.
adduser ckhoward #but enter your own username, of course
usermod -aG sudo ckhoward
ssh-copy-id ckhoward@ip #this works since we already generated the key
su - ckhoward #to switch to other user
chmod 700 ~/.ssh
nano .ssh/authorized_keys #this is where you paste the contents of your id_rsa pub file, cntrl x, y, ENTER
chmod 600 ~/.ssh/authorized_keys
exitOf course, test that all of this is working by ssh ckhoward@ip.
Install Apache Web server
DigitalOcean provides an alternative tutorial on installing the apache web server. A command is needed to let the firewall know that apache is okay. This is referred to as a rule. sudo ufw allow from 127.0.0.1 to any port 80 You can find your own IP address and only allow that, if you want, while you set up your server. This would have to be altered later on, if you expect others to hop on. If you would like to look at the rules you’ve set for allowing and denying connections, sudo ufw status numbered is a handy command. At this point, it should output:
[1] 80 ALLOW IN 127.0.0.1In my case, I set a rule for allowing only SSH connections from my IP address.
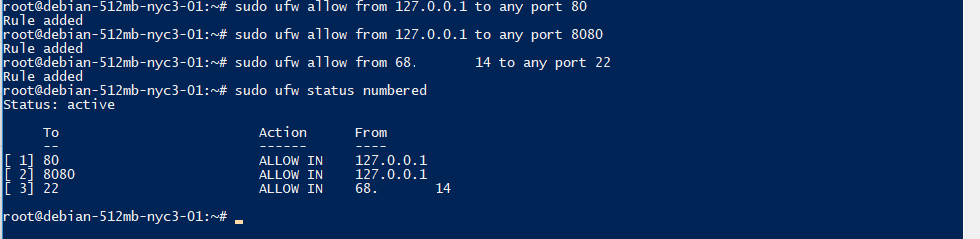
Installing apache2 and running it is trivial, enter the following commands:
sudo apt-get update
sudo apt-get install apache2
sudo systemctl start apache2.service
sudo systemctl status apache2
#if apache is running, enter:
hostname -I # this will give you a couple of IPs, enter them into your browser to find your siteAfter you’ve accessed your site from your browser, your activity should have been logged. You can check this with by finding and printing your logs with tail -f /var/log/apache2/access.log. There will be information associated with the request, the browser used, and the timestamp.
Install Tor
Run the command sudo apt-get install tor. Surprisingly simple. The Tor documentation instructs anyone deploying a hidden service to navigate to the torrc config file and uncomment the two statements:
#HiddenServiceDir /var/lib/tor/hidden_service/
#HiddenServicePort 80 127.0.0.1:80
Thus, we find the config file and edit it with the following:
find / -iname "torrc"
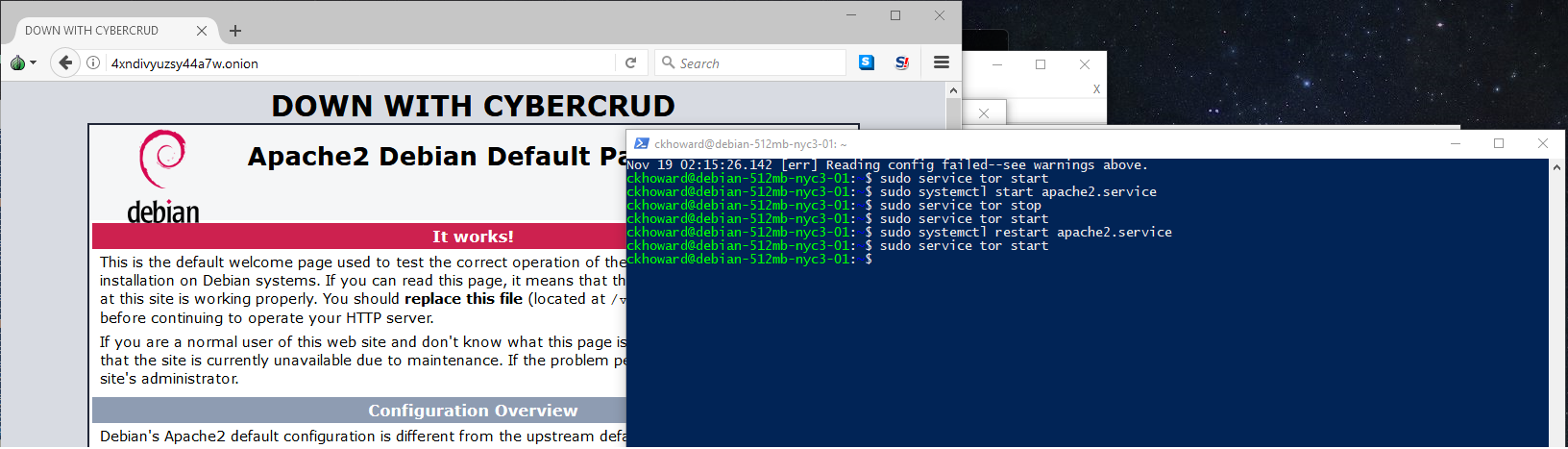
sudo nano /etc/tor/torrcIf the apache2 service is still running, let’s just restart that with sudo systemctl restart apache2.service. Start Tor with sudo service tor start. Tor is now running and has an associated Onion address. To find this address, run cat $HOME/hidden_service/hostname and the Onion address will print. This guide has set you up for the basics of getting a hidden service running with DigitalOcean. There are other guides on better practices for securing hidden services.
Credit goes to David Sidi for coming up with this idea in the form of a class assignment.